Have you ever found yourself staring at a blinking cursor on a server console, wishing you could control your network devices remotely? Picture this: your network is humming along smoothly, but a critical update needs to be applied to a switch. You don’t want to physically visit each switch and manually configure it, right? This is where Secure Shell (SSH) comes to the rescue. SSH empowers network administrators like you to securely manage and control network devices from anywhere in the world.
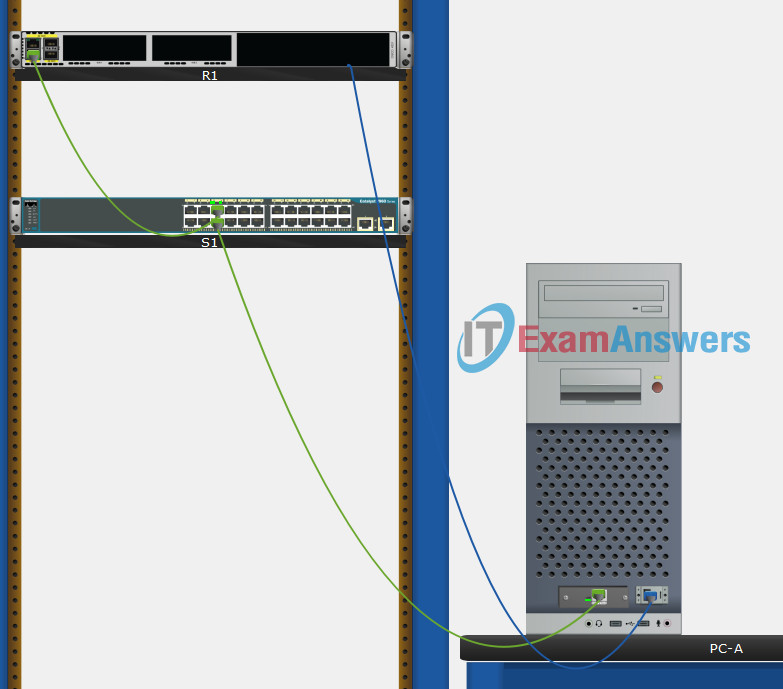
Image: itexamanswers.net
The 4.4.9 lab is an excellent starting point for understanding the complexities of SSH in a network environment. By working through this lab, you’ll learn how to establish secure connections, configure SSH settings, and manage network devices with precision. In this blog post, we’ll dive into the details of this lab, unpack the fundamentals of SSH, and equip you with the knowledge and confidence to master secure remote access in your network.
Secure Your Connection: The Power of SSH
SSH is like a digital tunnel connecting your computer to a remote network device, safeguarding your commands and sensitive data from prying eyes. It employs encryption, ensuring that every piece of information sent and received is scrambled and virtually impenetrable to unauthorized access. This is crucial for protecting your network from potential security breaches and vulnerabilities. The 4.4.9 lab utilizes SSH to connect to Cisco routers and switches, simulating real-world scenarios that you may encounter in your networking career.
Unlocking the Lab: Step by Step Guide
The 4.4.9 lab is a meticulously designed hands-on experience that guides you through the process of configuring SSH on network devices. Let’s break down the essential steps involved:
1. Understanding the Basics:
- Network Topology: Familiarize yourself with the network topology of the lab, understanding how routers and switches are interconnected.
- Host Machine: Ensure your host machine (the computer you’ll be using for the lab) is equipped with a terminal emulator like PuTTY.
- SSH Client: PuTTY is a readily available and popular SSH client for Windows, allowing you to connect to remote devices.
2. Configuring SSH on Routers:
- Enabling SSH: Navigate to the appropriate configuration mode on your router and enable the SSH service.
- Generating RSA Keys: Create strong RSA keys that will be used for authentication. Think of these keys as your digital passport, uniquely identifying your host machine.
- Setting a Password: You can optionally set a password to secure your SSH access, adding another layer of protection.
- Firewall Rules: Adjust firewall rules on your router to allow SSH traffic through. This ensures that your SSH connections can flow through the network smoothly.
3. Configuring SSH on Switches:
- SSH Access: Configure SSH access on your switches, ensuring that they are ready to receive SSH connections.
- Password Authentication: Use password authentication to grant access to designated users.
- Enabling SSH Banner: Consider displaying an SSH banner to inform users connecting to the device.
Putting Your Knowledge into Practice
The 4.4.9 lab provides a wealth of practical exercises that reinforce your understanding of SSH. You’ll have the opportunity to:
- Create Secure Connections: Establish SSH connections from your host machine to the network devices within the lab.
- Test Configuration: Send commands to the connected devices, verifying that your SSH setup is functioning correctly.
- Manage Network Devices: Perform basic configuration tasks on your connected devices using SSH, demonstrating how to apply your newfound skills.
- Troubleshoot Issues: Learn to identify and resolve common SSH issues, building your problem-solving skills.

Image: www.coursehero.com
Beyond the Lab: Real-World Applications
SSH is a cornerstone of modern networking, enabling secure management and control of devices in diverse environments. Imagine you’re managing a large enterprise network spanning multiple locations. SSH allows you to effectively:
- Deploy Configuration Updates: Safely distribute configuration changes across numerous network devices from a central location.
- Monitor Network Health: Use SSH to retrieve system information, performance metrics, and logs from network devices, gaining insights into their operational status.
- Troubleshoot Network Issues: Diagnose and resolve network problems remotely by inspecting device logs and configuring troubleshooting tools.
Expert Insights: Mastering the Art of SSH
Mastering SSH involves more than just configuring its settings – it’s about adopting best practices for secure and efficient remote access:
- Strong Passwords: Emphasize the importance of using complex and unique passwords for your SSH accounts, safeguarding them from unauthorized access.
- Two-Factor Authentication (2FA): Consider implementing 2FA as an additional layer of security. This requires users to provide two forms of authentication, such as a password and a code sent to their mobile device, for greater protection.
- Key Management: Adopt a structured approach to managing your SSH keys, ensuring proper storage, backup, and revocation processes. This minimizes the risk of key compromise and unauthorized access.
- Regular Updates: Keep your SSH software and network device firmware up to date with the latest security patches to plug vulnerabilities and mitigate potential security risks.
4.4.9 Lab – Configure Network Devices With Ssh
Embrace the Power of SSH
The 4.4.9 lab provides a foundation for mastering SSH, a fundamental technology that empowers you to securely connect and manage network devices. By completing this lab and adopting best practices, you’ll be well-equipped to handle the complexities of remote access in modern networking environments. As you gain proficiency in SSH, you’ll become a more efficient and secure network administrator, effectively managing network resources from anywhere in the world. Don’t hesitate to explore additional resources, delve into advanced SSH concepts, and continue honing your network management skills.
Let this lab empower you to become a confident and skilled network administrator who embraces the power of secure remote access.






